監管指引
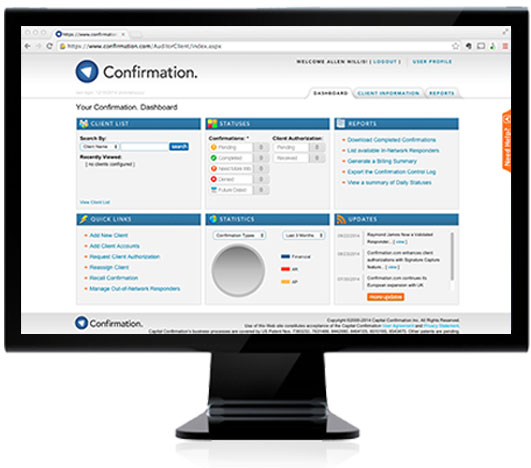
Confirmation.com helps auditors comply with auditing standards and requirements
Learn how Confirmation.com complies with each of the governing bodies.
AICPA
AU-C Section 500: Audit Evidence
| 指引 | How Confirmation.com complies |
|---|---|
| 外部詢證函 .A18外部詢證函代表核數師所取得的審計證據,由第三方(詢證方)以紙本、電子或其他方式直接向核數師以書面回應的形式提供。 |
Confirmation.com uses a unique authentication and authorization process to verify the authenticity of each user. By sending a request to a validated responder, you eliminate the burden of having to verify the identity of the respondent and whether or not they are authorized to respond. |
| Reliability .A32 While recognizing that exceptions may exist, the following generalizations about the reliability of audit evidence may be useful:
|
Confirmation.com uses a unique authentication and authorization process to verify the authenticity of each user. By sending a request to a validated responder, you eliminate the burden of having to verify the identity of the respondent and whether or not they are authorized to respond. Undergoes SOC 1, SOC 2 and SOC 3 examinations every six months, and has received an ISO 27001 certification of its Confirmation.com service. |
AU-C Section 505: External Confirmations
| 指引 | How Confirmation.com complies |
|---|---|
| 選擇合適的詢證方 .A3 Responses to confirmation requests provide more relevant and reliable audit evidence when confirmation requests are sent to a confirming party who the auditor believes is knowledgeable about the information to be confirmed. |
Confirmation.com uses a unique authentication and authorization process to verify the authenticity of each user. By sending a request to a validated responder, you eliminate the burden of having to verify the identity of the respondent and whether or not they are authorized to respond. |
| Reliability of Responses to Confirmation Requests .A15 An electronic confirmation system or process that creates a secure confirmation environment may mitigate the risks of interception or alteration. Creating a secure confirmation environment depends on the process or mechanism used by the auditor and the respondent to minimize the possibility that the results will be compromised because of interception or alteration of the confirmation. |
Uses the highest level of security to ensure privacy and data integrity. Undergoes SOC 1, SOC 2 and SOC 3 examinations every six months, and has received an ISO 27001 certification of its Confirmation.com service. |
Practice Alert 03-1: Audit Confirmations
| 指引 | How Confirmation.com complies |
|---|---|
| .19 If the auditor is satisfied that the electronic confirmation process is secure and properly controlled, and the confirmation is directly from a third party who is a bona fide authorized respondent, electronic confirmations may be considered as sufficient, valid confirmation responses. | Undergoes SOC 1, SOC 2 and SOC 3 examinations every six months, and has received an ISO 27001 certification of its Confirmation.com service. Uses the highest level of security to ensure privacy and data integrity. Confirmation.com uses a unique authentication and authorization process to verify the authenticity of each user. By sending a request to a validated responder, you eliminate the burden of having to verify the identity of the respondent and whether or not they are authorized to respond. |
PCAOB
AU Section 330: The Confirmation Process
| 指引 | How Confirmation.com complies |
|---|---|
| Respondent .27 The auditor should consider whether there is sufficient basis for concluding that the confirmation request is being sent to a respondent from whom the auditor can expect the response will provide meaningful and appropriate audit evidence. |
Confirmation.com uses a unique authentication and authorization process to verify the authenticity of each user. By sending a request to a validated responder, you eliminate the burden of having to verify the identity of the respondent and whether or not they are authorized to respond. |
| Performing Confirmation Procedures .29 During the performance of confirmation procedures, the auditor should maintain control over the confirmation requests and responses. Maintaining control means establishing direct communication between the intended recipient and the auditor to minimize the possibility that the results will be biased because the interception and alteration of the confirmation requests or responses. |
Uses the highest level of security to ensure privacy and data integrity. Allows an auditor to send audit confirmation requests directly to the intended responder. Undergoes SOC 1, SOC 2 and SOC 3 examinations every six months, and has received an ISO 27001 certification of its Confirmation.com service. |
AU Section 326: Audit Evidence
| 指引 | How Confirmation.com complies |
|---|---|
| Sufficient Appropriate Audit Evidence .08 Audit evidence is more reliable when it is obtained from knowledgeable independent sources outside the entity. |
Undergoes SOC 1, SOC 2 and SOC 3 examinations every six months, and has received an ISO 27001 certification of its Confirmation.com service. |
ISA
ISA - ISA 505: External Confirmations
| 指引 | How Confirmation.com complies |
|---|---|
| Para 6(a) Definition: External Confirmation 審計證據由第三方(詢證方)以紙本、電子或其他方式直接向核數師以書面回應的形式提供。 |
Confirmation.com enables auditors to receive audit confirmations electronically. Responses are prepared by authorized bank officials based on the auditor's request. Use of Confirmation.com meets the requirements of an ‘External Confirmation’. |
| Para 7 Maintaining control 當使用外部詢證程序時,核數師應持續掌控外部詢證函請求。 |
Auditors keep complete control over the process, including client and accounts setup, requesting client authorization and the sending and receipt of confirmations. |
| A2 Selecting the appropriate confirming party 如果向核數師認為瞭解待詢證資訊的詢證方傳送詢證函請求,對詢證函請求的回應可以提供更相關、更可靠的審計證據。例如,瞭解所需詢證函交易或安排的金融機構官員可能是相關金融機構中最適合受理詢證函請求的人選。 |
Participating banks have strict user access controls and monitoring procedures in place to ensure that only authorized bank officials respond to audit requests through Confirmation.com. |
| A6 Validating addresses 確認請求傳送地址是否正確,包括在傳送詢證函請求之前,測試其中部份或全部地址的有效性。 |
We validate all entities participating in the Confirmation.com network. The controls surrounding this process are included in our SOC 1 report that is issued every six months as part of our controls audit. By relying on our validation procedures, you avoid the need to perform your own validation procedures. |
| A12 Electronic responses 以電子方式(例如透過傳真或電子郵件)收到的回應涉及可靠性風險,因為可能難以確認回應方的來源及授權,並且可能難以偵測篡改內容。核數師及回應方使用的程序可以為透過電子方式接收的回應建立安全的環境,從而可以減低此類風險。如果核數師對此類程序的安全性及適當控制感到滿意,則會提高相關回應的可靠性。 電子詢證程序可以結合各種技術來驗證以電子形式傳送資訊人士的身份,例如透過使用加密技術、電子數碼簽名及程序驗證網站真實性。 |
Confirmation.com's operates industry-leading information security and data privacy practices. We have procedures and controls in place to ensure the integrity, confidentiality and accessibility of data. We undergo third-party audits to demonstrate the effectiveness of our controls:
|
| A13 Involvement of third parties 如果詢證方使用第三方來協調並回應詢證函請求,核數師可以執行程序來應對以下風險:(a) 回應可能並非來自適當的來源;(b) 回應方可能無權作出回應;(c) 傳輸的完整性可能已被損害。 |
Confirmation.com's control environment ensures that user access if controlled and monitored at the banks, and that transmission of data is secure and maintains integrity. Our controls reports outlined above demonstrate the effectiveness of these procedures. |
| Para 12 Non-responses 每當出現對方不回應的情況,核數師應執行替代審計程序,以獲得可靠的相關審計證據。 |
Confirmation.com guarantees responses for In-Network confirmations, avoiding the need for alternative procedures. |
Auditors send millions of requests worldwide to their clients' banks, law firms and suppliers. Online confirmations make this process simple.